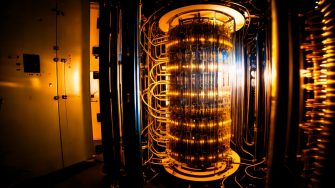
Cyber experts warn of looming “quantum hacking” threat: quantum computers could reduce the time to hack encrypted data from a million years to a single day
Cyber security experts have warned that within the next decade, cryptographically encrypted data - currently considered the gold standard for securing data - could be decrypted as cybercriminals and nation states develop quantum computing capabilities.